What is Two-Step Verification and do I need it?
If you read our last edition of TekkieNews, explaining what to do if you suspect someone has hacked your online accounts, such as Gmail, Yahoo, Facebook, DropBox and others, you will know that we recommend you enhance account security by setting up two-step authentication, also referred to as two-factor verification.
This security measure has been widely adopted by some of the most popular online services and it is usually an opt-in feature. Not sure how if works or whether you need it? This article will explain everything for you.
So, what is Two-Step Verification?
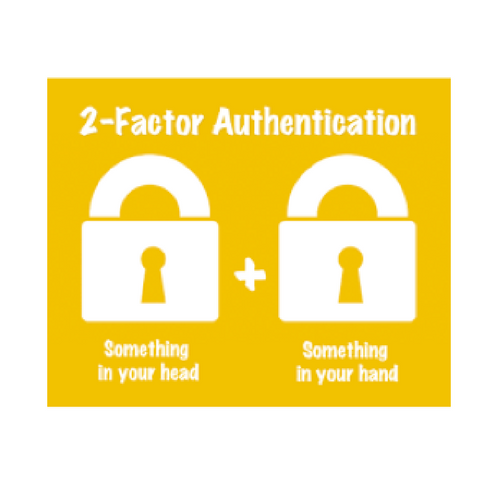
As its name indicates, two-step verification focuses on the authentication process, one of the most crucial aspects of account security. When you go to any of your accounts, unless the site “remembers” you, you are prompted to provide your credentials. This is how you authenticate yourself, telling the site, “This is me, and here’s my password to prove it”. For many years, this type of security was enough to verify your identity and determine whether to allow access to your account.
Why do I need Two-step Verification?
Unfortunately, username plus password just doesn’t cut it anymore. As discussed in our previous article, cyber criminals are targeting consumers like you and me, through “phishing”. Phishing involves ways to deceive you in supplying your private account information so that the fraudsters can gain access to your accounts. Once they gain access they use your personal information to commit identity theft, charge your credit cards, read your emails, set up PayPal accounts and empty your bank!
Adding more security questions doesn’t help either, since criminals can add those questions to their phishing sites or harvest the information using malware. All of these security questions and requirements involve what the user knows, and if the user knows it, cyber criminals can find out! That is why two-step verification is so useful: It’s not about what the user knows but what the user has in hand.
How does Two-Step verification work?
With two-step verification, users must prove that they are using a certain device and that the device is in their possession. How do you prove this? If it’s a mobile phone, the service sends a text message to your phone with a code that’s different every time you log in. To gain entry to that site/ app, you’ll then need to enter that unique code. This way you are not just saying, “this is me and here’s my password to prove it”, but also, “I have my unique code with me and here is to prove it!” – Extra security making you super safe.
Yes, you do need Two-Step Verification!
Do we recommend setting up two-factor authentication? Absolutely. You may think it will be annoying taking this extra step every time you log into an account, however, you only need to do when accessing your account on a different device and it dramatically improves your account’s security, protecting your personal information. Like we said, username and password just don’t cut it anymore.
How to activate Two-Step verification?
Depending on which account you have, two-step verification should be relatively easy to activate. Here are some instructions for some of the most popular accounts:
- Gmail: With two-step verification, Google will require that you enter a unique code that that will appear on the “Google Authenticator” app on your mobile, providing you with an important extra layer of security. You can use “Remember me” option to disable this step for any device, such as your laptop or smartphone, that you use regularly.
- Facebook: Go to your Facebook Security page. Under “Login Approvals”, check the box to require a security code to access your account from unknown browsers.
- DropBox: Visit the Security page and click “Enable” under Two-Step verification at the top of the page.
- Yahoo: Simply click on the button to the right of the “Two-step verification” option on the Account Security page.
Twitter: Go to your Twitter Security and Privacy page, which can be found on the right-side menu on the Settings page. Once there, activate login verification. With login verification enables, Twitter will send a message to either your phone or the Twitter app based on your selection, requiring that you approve any new devices that are trying to access your account.
If you need help with either enhancing account authentication or help if your account has been hacked or compromised, we have the expertise to help – just call us on 81138682.